There are many situations where mocking your location becomes useful——whether it's for gaming (like Pokémon GO), using dating apps in different regions, or testing app behavior in various locations. However, many modern apps can detect if you're faking your GPS and may block or ban your account. That's where the concept of hide mock location comes in. In this guide, we'll explain what it means, when you need it, and how to hide mock location with or without rooting your Android device.
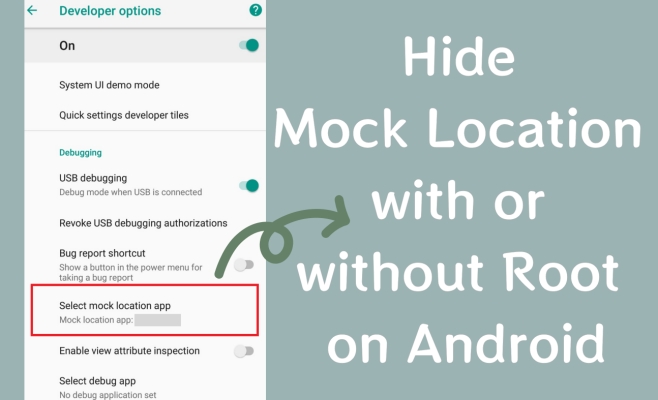
- Part 1. What Is Hide Mock Location on Android?
- Part 2. How Hiding Mock Location Works [Root vs. No Root]
- Part 3. How to Hide Mock Location with Root
- Part 4. How to Hide Mock Location without Root
- Part 5. Conclusion
Part 1. What Is Hide Mock Location on Android?
Mock location on Android means faking your device's GPS position using a special app or tool, usually enabled in Developer Options. People use this to test apps or spoof their location for games and region-locked services. However, many apps can detect mock locations and may block features, show errors, or ban users. Hide mock location is a method that conceals the fact you're using a fake GPS, making apps believe your spoofed location is real. This helps you avoid detection, prevents app crashes, and reduces the risk of bans while using location-based apps smoothly.
Part 2. How Hiding Mock Location Works [Root vs. No Root]
To hide mock location on Android, you can use either of two approaches: with root access or without it. Rooting gives deeper system control and is more effective but riskier and more technical. Comparingly, non-root methods are safer and easier. Below is a comparison of both methods:
| Type | Hide Mock Location Without Root | Hide Mock Location With Root |
|---|---|---|
| Difficulty | ⭐ | ⭐⭐⭐ |
| Tool | MagFone Location Changer | Magisk, Xposed, LSPosed |
| Safety | Safer, no risk of bricking device | Risk of data loss, warranty void |
| Time | Quick | A Little Long |
Part 3. How to Hide Mock Location without Root
MagFone Location Changer is a powerful tool that helps you hide mock location on Android devices without requiring root access. It allows you to spoof your GPS location smoothly and bypass detection from apps that typically flag mock locations. This approach is safe and user-friendly, making it an excellent choice for anyone who wants to simulate locations discreetly without risking device security or warranty. Next is a simple guide for you.
MagFone Location Changer
Easily change your GPS location on iOS and Android devices to anywhere with one click, while not requiring root or jailbreaking!
Step 1 Set Up MagFone Location Changer
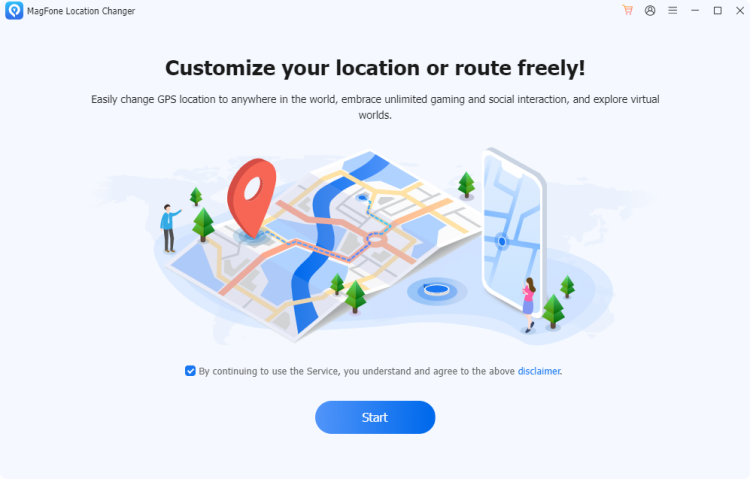
Download MagFone Location Changer from the official website and install it. Fire up the program and link your Android device. Turn on Developer Mode and Location Services to ensure the app detects your iPhone. Once detected, tap Change Location on the screen.
Step 2 Select and Apply Your Desired Location
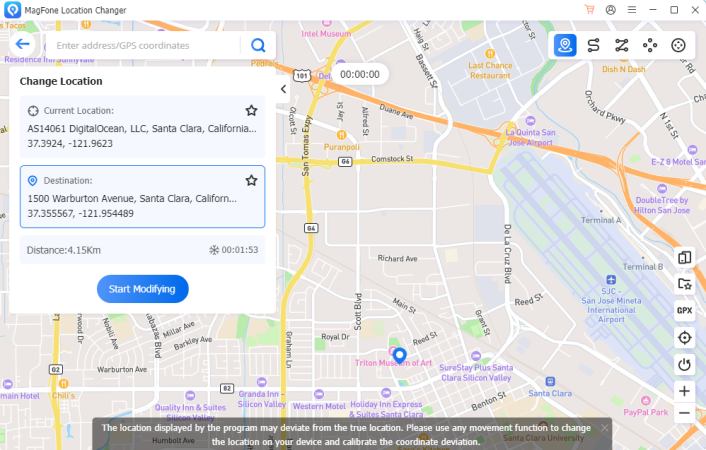
A map interface will open where you can search or zoom in to pick your preferred location. After selecting the spot, click Start Modifying to apply the fake location. Your apps, like BeReal, will now reflect this new location for posting or other uses.
Part 4. How to Hide Mock Location with Root
Rooting your Android device gives you advanced control over system-level behaviors, including the ability to hide mock location from detection. By combining Magisk with powerful frameworks like LSPosed or Xposed, you can effectively mask GPS spoofing from apps that detect and block fake locations, such as games, banking apps, or social platforms. Next is how to hide mock location from apps.
To get started, you need to root your device with Magisk, which is required for installing LSPosed or Xposed modules:
Step 1. Back up your device data to prevent loss during the process.
Step 2. Unlock your device's bootloader (using OEM-specific commands or tools). Then Install a custom recovery like TWRP.
Step 3. Flash the Magisk ZIP file via recovery to gain root access. After that, reboot and verify root using a root checker app.
Step 4. Open the Magisk app, which now manages modules, root permissions, and SafetyNet bypass.
Option 1. Hide Mock Location with LSPosed
LSPosed is an advanced framework for rooted Android devices, designed to manage and run modules that can hide mock locations effectively. Unlike traditional Xposed frameworks, LSPosed supports Android 10+ with better stability and security. It allows users to hook system functions and mask any spoofing attempts without causing system crashes.
Step 1. In the Magisk app, install LSPosed (you can download the LSPosed ZIP and flash it via Magisk).
Step 2. Reboot your device and open the LSPosed manager app.
Step 3. Enable the module and apply it only to apps you want to spoof location for.
Step 4. Reboot again and test using a detection app (like SafetyNet Checker or Mock Mock Locations).
Option 2. Hide Mock Location with Xposed
Xposed Framework allows deep system-level customization on rooted Android devices and supports a variety of modules to hide mock locations. It's an older but reliable method mainly compatible with Android versions below 10. The framework hooks into system APIs to disguise spoofed GPS data.
Step 1. Root your Android device with Magisk, then flash the correct Xposed Framework ZIP for your Android version via custom recovery (like TWRP).
Step 2. Reboot your device and install the official Xposed Installer app to manage modules.
Step 3. Inside Xposed Installer, search for and download a module such as Hide Mock Location.
Step 4. Activate the module within the Xposed Installer and reboot your phone to apply changes.
Step 5. Open the module settings and configure it to hide mock location from selected apps that you want to spoof location for.
Part 5. Conclusion
Hiding mock location on Android is essential for users wanting to spoof GPS without app detection. Whether rooted or not, tools like MagFone Location Changer and frameworks like Magisk or LSPosed offer effective solutions. Choose the method that best suits your device and technical comfort, always remembering to consider app policies and device security.

